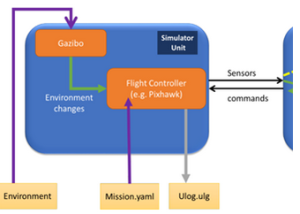
Simulation of Security attack scenarios
- Supervisor(s): Prof. Avi Mendelson
- Requirements: Good programming skills, course / knowledge in security attacks (optional)
- Status: available
This project is based on the Master Thesis of Mr. Kfir Girstein and on the SW package he developed. The purpose of the project is to extend the tool and add a graphical interface to it.
Students who decide to continue their research could add to the tool additional sophisticated features such as internal and external events.
Anomaly Detection of Real-time Systems
- Supervisor(s): Roman Maltis, Prof. Avi Mendelson
- Requirements: Good programming skills, Deep Learning on Computation Accelerators (236781)
- Project document
- Status: available
This project aims to examine the effectiveness of HTM algorithms in order to detect security attacks on systems.
The project will have 2 parts:
- Run an existing HTM algorithm on tagged data.
- Improve the algorithm.
If successful, the work can be extended into a Master Thesis
Remote Side-Channel attacks
- Supervisor(s): Prof. Avi Mendelson
- Requirements: Computer Architecture (236267), course / knowledge in security attacks (optional)
- Status: available
Recently, we published a paper “The Use of Performance-Countersto Perform Side-Channel Attacks” that shows that under some conditions, a user can use performance counters to perform remote attacks (i.e., without physical access to the device).
This project aims to extend the experiments being presented in the paper and extend the usage model from Intel X86 to ARM-based platforms.
The code being used for the paper will be provided.
Sub-circuit Recognition Using Graph Neural Networks (GNN)
- Supervisor(s): Leonid Azriel
- Requirements: Introduction to Machine Learning (236756), מערכות ספרתיות ומבנה המחשב (00044252)
- Project document
- Status: available
In this project, we will evaluate a GNN-based method of sub-circuit recognition proposed by a recent research paper.
Analysis and Improvement of the Ibex RISC-V Dummy Instruction Insertion Attack Countermeasure
- Supervisor(s): Leonid Azriel
- Requirements: Computer Architecture (236267)
- Project document
- Status: in talks
The goal of this project is investigation and potentially an enhancement of effectiveness of this feature against real attacks.
Design of a DPA-protected ALU
- Supervisor(s): Leonid Azriel
- Requirements: (00044157) מעבדה בהנדסת חשמל 1א
- Project document
- Status: available
Parametric Attack on a Physical Unclonable Function (PUF)
- Supervisor(s): Leonid Azriel
- Requirements: מערכות ספרתיות ומבנה המחשב (00044252), (00044157) מעבדה בהנדסת חשמל 1א
- Project document
- Status: available
In this project, we are interested to learn about a parametric attack on PUFs mounted by a malicious manufacturing facility.
Hardware Vulnerability Detection Using Graph Neural Networks (GNN)
- Supervisor(s): Leonid Azriel
- Requirements: Algorithms 1 (234247), Introduction to Machine Learning (236756), מעבדה בהנדסת חשמל 1א (00044157), (00044252) מערכות ספרתיות ומבנה המחשב
- Project document
- Status: available
In this project, we are interested to check the machine learning ability to detect security vulnerabilities. In particular, we will apply the Graph Neural Network techniques to that task.
AI-based Synthetic Benchmark Generator for Hardware Security
- Supervisor(s): Leonid Azriel
- Requirements: מערכות ספרתיות ומבנה המחשב (00044252), Algorithms 1 (234247), Introduction to Machine Learning (236756) – recommended, (00044157) מעבדה בהנדסת חשמל 1א
- Project document
- Status: available
However, the number of logical circuits openly available is limited and therefore cannot serve a sound base for training. The industry needs a way to obtain benchmarks in large amounts. A possible solution is creating synthetic benchmarks based on reference authentic examples.